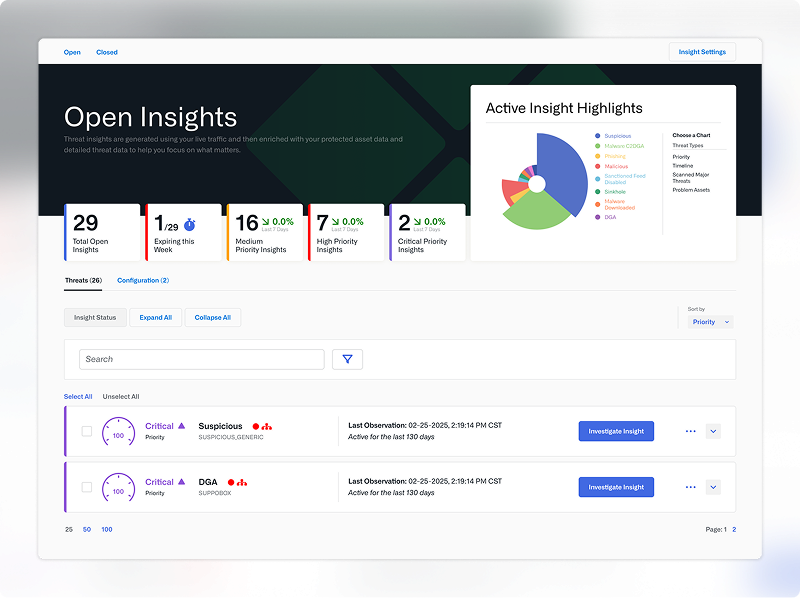
Threat actors are outpacing current security tools
Threat actors use AI to create malware variants to rapidly evade traditional security measures. They use cloaking and massive threat distribution systems (TDSs) to direct victims through a maze of domains to efficiently deliver malicious content at scale while evading detection. Standard security tools can’t keep up.
Infoblox Threat Defense™ closes this gap by monitoring 180,000+ threat clusters and blocking TDS domains, keeping your devices, users and cloud workloads safe without needing a patchwork of security tools.
BENEFITS
Why Infoblox Threat Defense?
PRODUCT DETAILS
Infoblox security products
Take a more proactive security stance using predictive threat intelligence and algorithmic protections while boosting the efficiency of investigation and response.
SOC Insights applies AI analytics to security events, networks, assets and unique DNS threat intel data to distill tens of thousands of alerts to a handful, helping you uncover hidden threats and enhance SOC efficiency with enriched asset visibility.
Lookalike domains are a growing threat that deceives victims and negatively impacts your brand. Threat actors use thousands of them, but Infoblox’s proactive monitoring can help you identify these threats early and avoid brand compromise.
Threat actors use creative domain names to support a wide variety of attacks. Infoblox can leverage its deep ties with global regulators, ISPs, registrars and law enforcement to validate and take down domains that threaten you or your brand.
The Infoblox Security Ecosystem maximizes existing security investments while enhancing security by seamlessly integrating with various tools, enabling real-time threat detection and response, automating tasks and improving operational efficiency.
PRODUCT VIDEO
Detect threats faster with Infoblox Threat Defense

Aflac enhances cyberthreat intelligence and integrates security ecosystem with Infoblox
The Challenge
- Secure corporate cloud-first initiative efforts
- Enhance threat intelligence and reporting capabilities
- Integrate cybersecurity ecosystem to uplift security stack
The Solution
- Enhanced threat intelligence and reporting
- Optimized security ecosystem integration
Products Used
- Infoblox Threat Defense Advanced
Scott Wilson
Senior Security Administrator, Aflac
“We needed to integrate our diverse portfolio of cybersecurity tools and applications for better threat intelligence and reporting in real time. Infoblox runs on the architecture I already have, allowing my team to automatically provide aggregated threat data to the rest of the security ecosystem for investigation and remediation if necessary.”
Infoblox Threat Defense boosts Bochum University’s defenses against phishing and other threats
The Challenge
- Protect against external security threats, specifically phishing
- Ease the IT team’s workload
- Guarantee “teaching freedom”
The Solution
- Protection from phishing and other cyberattacks
- Transparency via comprehensive analysis options
- Simple installation and minimal maintenance
Products Used
- Infoblox Threat Defense
- Infoblox NIOS DDI
Martin Schindler
Head of Network & Security, Bochum University
“The deciding factor was that Infoblox was able to meet our individual requirements and managed to give us a sense of security—and we are extremely pleased about that!”
Askari Bank modernizes and enhances its cybersecurity posture with Infoblox Threat Defense Advanced
The Challenge
- Strengthen overall security posture
- Apply DNS behavior monitoring to detect data exfiltration, DGAs, DNSMessenger, etc.
- Block exploits, phishing, ransomware and other modern malware
- Protect Askari brand with Lookalike Domain Monitoring
The Solution
- Faster threat detection
- Reduced incident response times
Products Used
- Infoblox Threat Defense Advanced
Jawad Khalid Mirza
CISO, Askari Bank
“As we ran the PoC through various scenarios, there was not a single instance of a successful data infiltration or exfiltration event. Seeing Infoblox Threat Defense in action blocking malicious activity in our own environment gave us a lot of confidence in the Infoblox solution.”
Bed Bath & Beyond Mexico achieved technological independence with Infoblox Threat Defense and DDI
The Challenge
- Gain greater autonomy over IT processes, incidents and needs
- Resolve infrastructure management challenges, including lack of visibility, slow response times and insufficient data
The Solution
- Three-week migration without a single service interruption
- Full threat visibility across the entire infrastructure with nothing more than an internet connection
- Improved threat management
Products Used
- Infoblox Threat Defense
- Infoblox Universal DDI™
Martin Moriyama
IT Director, Bed Bath & Beyond Mexico
“The whole migration was completed with zero service interruptions to customers. We continued to operate both in shops and offices in a seamless way.”
San Francisco sharpens visibility to strengthen its security posture
The Challenge
- Improve network visibility for enhanced defense against ransomware, phishing and web spoofing attacks
- Strengthen the team’s ability to detect and counteract the impact of lookalike domains
- Ensure uninterrupted uptime for over 17,000 employees, first responders, elected officials and residents
The Solution
- Automatic data collection and analysis eliminate blind spots and deliver comprehensive insights for superior security
- Real-time threat intel to enforce new rules, stop attacks and prevent potential damage
- Adaptable security for remote workers for peace of mind regardless of location
Products Used
- Infoblox Threat Defense
- Infoblox NIOS DDI
Nathan Sinclair
Cyber Defense Operations Manager, The City and County of San Francisco
“With Infoblox, we have much more complete context around and insight into our security data. Instead of us trying to figure out and correlate the data and understand something like, how are DNS requests going to this website? Before, it was a lot of work to do that. But not anymore. Infoblox took that guesswork out.”
Find threats other tools miss
Infoblox Threat Defense uses unique DNS threat intelligence and algorithmic protections to detect threats other tools miss, transforming security effectiveness by uncovering hidden malicious traffic that relies on DNS.
| Key Capability | Description | Infoblox Threat Defense | NGFW | SAS | EDRE |
| Enterprise-Wide Secure Resolver and DNS Query Logging | Uses DNS query data to find and convict domains | ||||
| Full DNS Behavior Monitoring | Monitors all DNS record types for malicious activity | ||||
| Lookalike/Doppelganger Domain Detection & Takedown | Mitigate lookalike/doppelganger attack surface | ||||
| Zero Day DNS Protection | Identifies new or emerging domains for your organization that could pose a threat | ||||
| Behavior-Based DNS Tunneling Detection | Detects DNS tunnels being used for data exfiltration/infiltration, C2 communications, etc. | ||||
| Proactive Suspicious/High-Risk Domain Protection | Identifies and blocks suspicious domains preemptively that are likely to be used in future malicious campaigns | ||||
| Automatic, Native Context Enrichment | Correlates network context without the need for clients or sinkholing (user, device, source IP, location, MAC address, VLAN) | ||||
| Proactive Threat Distribution Systems (TDS) Detection and Disruption | Identifies threat actor TDS infrastructure, not just individual domains, to counter threat actors rotating across numerous domains to evade detection |
KEY CAPABILITIES
Threat Defense key capabilities
Infoblox Threat Defense is an industry-leading Protective DNS solution that proactively secures the entire modern enterprise.
Enjoy highly predictive threat intelligence that tracks near–real-time threat clusters and TDS to block threats, including those that use evasive techniques. Or apply algorithmic detections to customer DNS traffic to block Zero Day DNS, data exfiltration and DGAs.
Manage insider risks by monitoring high-risk application usage or blocking unsanctioned applications. Our application discovery feature provides full visibility and control over applications and technologies, like file sharing and generative AI.
Threat actors use lookalike domains to deceive users into visiting malicious websites. Increasingly creative and targeted, these domains pose a growing threat to organizations. Infoblox protects against common lookalikes and can monitor for targeted lookalikes.
Submit your domains for lookalike monitoring, and when a threat is identified, leverage takedown services to eliminate threats to your users, customers or brand quickly.
Quick user and device attribution speeds up investigations and incident response, giving your analysts the “who, what, where” context around security events without browsing through logs or using other manual approaches.
Leverage intelligent ecosystem integrations to share threat intelligence and other data, automate incident response and generate powerful insights to optimize security capabilities across the security stack.
You’re in good company trusted by …
WHAT EXPERTS SAY ABOUT OUR PRODUCTS
Security analysts on the value of DNS in cybersecurity
This [DNS] visibility is invaluable for forensic investigations and monitoring devices that cannot host traditional security agents such as operational technology devices.”
As XDR architectures and portfolios evolve to ingest more data and use that data more effectively, security teams and their vendors should consider how DNS Detection and Response (DNSDR) can enhance XDR.”
- IDC Market Perspective on Infoblox DNS Detection & Response
This [DNS] visibility is invaluable for forensic investigations and monitoring devices that cannot host traditional security agents such as operational technology devices.”
- HardenStance on DNS Detection and Response as part of XDR
As XDR architectures and portfolios evolve to ingest more data and use that data more effectively, security teams and their vendors should consider how DNS Detection and Response (DNSDR) can enhance XDR.”
RESOURCES
Additional Threat Defense resources
Explore key resources to learn more about Infoblox Threat Defense and related security offerings.
Datasheets
We offer Infoblox Threat Defense with multiple packages and components, so you can get the best use-case solution for your needs.
Infoblox Threat Defense Advanced
Stop threats other solutions miss and often before threat actors launch their attack.
Infoblox Threat Defense Business Cloud
Strengthen and optimize your security posture from the foundation.
Infoblox Threat Defense On-Premises
Secure existing networks and digital transformations like SD-WAN, IoT and cloud leveraging existing infrastructure.
Infoblox Threat Defense Essentials
Block ransomware, phishing, exploits and other modern malware using Infoblox Threat Intel.
Solution Notes
Learn about the essential and robust features and capabilities Infoblox Threat Defense offers.
Infoblox Threat Defense Package Comparison
Explore the differences in the Infoblox Threat Defense product line to determine which package aligns with your specific visibility and security requirements.
Discover the key barriers hindering Security Operations Center (SOC) efficiency and how AI-driven SOC Insights offer unique solutions to address these challenges.
TIDE (Threat Intelligence Data Exchange
Drive SecOps efficiency with threat intelligence management and automation.
Videos
Watch videos from our customers and Infoblox experts about how Infoblox Threat Defense helps you achieve your security goals.
Simplify visibility and control
Truma paves the way with enhanced network visibility and security from Infoblox.
Take control of with multi-cloud
Maximize multi-cloud efficiency with Infoblox.
Detect threats faster with Infoblox Threat Defense.
Identify attacked devices for greater context with Infoblox Threat Defense.
Accelerate investigation and response
Investigate security incidents up to 67 percent faster.
Automate integrated threat intelligence across your security stack.
GET STARTED
Want to strengthen your cybersecurity? Let’s talk.
Resilient network security and SecOps efficiency starts with Infoblox.
Share your questions, concerns and priorities with an expert to get the specific answers you need to understand how Infoblox Threat Defense can improve your defensive posture and uplift SecOps efficiency.
After contacting us, our team will be in touch within one business day.
- Talk to an Expert
Resilient network security and SecOps efficiency starts with Infoblox.
Share your questions, concerns and priorities with an expert to get the specific answers you need to understand how Infoblox Threat Defense can improve your defensive posture and uplift SecOps efficiency.
After contacting us, our team will be in touch within one business day.
- Register for Security Workshop